“The Internet was built without an identity layer.”
– Kim Cameron, Chief Architecture of Identity, Microsoft
When Tim Berners-Lee wrote the Whitepaper for the World Wide Web in 1989, he was mainly concerned with organizing information for projects at CERN. He wanted it to be easy to store, share, and retrieve information in a distributed manner to minimize information loss and maximize collaboration. To this end, he developed “Mesh”, a global hypertext system.
“CERN meets now some problems which the rest of the world will have to face soon. In 10 years, there may be many commercial solutions to the problems above, while today we need something to allow us to continue.”
At the time, Berners-Lee already had a vision for something bigger. As the quote above indicates, he expected Mesh to become a blueprint for the entire world. From the beginning, it was all about empowering users. The requirements listed “non-centralization” and “private links”, whereas non-requirements included “copyright enforcement” and “data security”. And while these were practical requirements, they shaped the philosophical ethos of the web – a place of freedom, collaboration, accessibility, and anonymity.
The Tragedy of the Information Producer
Just like Bitcoin today, the early web struggled immensely with piracy. As soon as the MPEG-1 Audio Layer 3 (MP3) standard was developed, file sharing emerged. And while authorization and accounting systems were proposed as hypotheticals by Berners-Lee, they were never actually implemented. The circumstances gave rise to protocols like Direct Connect (DC) and platforms such as Napster, enabling users to connect, share, and download files ad infinitum.
What I call the Accountability Assymetry, was the first time information producers and suppliers faced a severe threat posed by the web. Consumers gained access to any Intellectual Property (IP) digitized at the time, while producers failed to enforce their copyright.
Contrary to the physical world, the web constitutes a frictionless environment with anonymous agents. Neither are the costs of conducting a crime high nor can you be identified post factum. While the physical stack got passports to provide identity and life, liberty, and property to enforce accountability, the web stack employs indiscriminate protocols with the sole focus on delivering information to the masses.
From Electrons to Pixels: Understanding the Internet Stack
To understand why the web lacks an identity layer, we must examine the internet stack, known as the Open Systems Interconnection (OSI) model.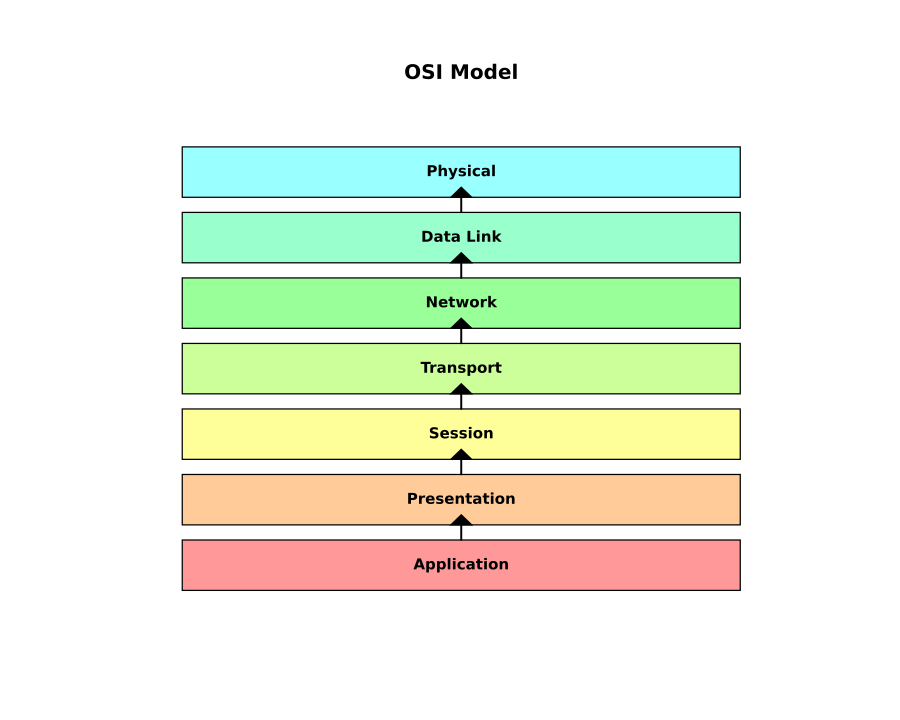
As the above image illustrates, the OSI model has seven distinct layers, each of which either generates (L7), translates (L6), or transmits (L1 – L4) data. Layer 5 ensures that users can exchange data reliably because, as the name “web” suggests, the Internet is an intertwined network of clients (users) and servers (vendors), while the World Wide Web is an intertwined network of information producers and consumers.
Throughout the routing of data packets, neither the client nor the server reveals the identity of the actual owners. Instead, at layers 1-2, MAC addresses are used within an intranet, whereas layers 3-7 utilize IP addresses and ports within both the intranet and the internet. The only way our state name could ever be revealed is within the WWW building on layer 7. We see this with applications such as Facebook and Twitter, where people sign up with their state names. Furthermore, this is crucial for services such as online banking, government portals, and e-commerce sites to ensure authenticity, enhance security, and comply with the law.
For the most part, the initial authentication for these services relies on the physical identity stack built by governments. Thus, trusted parties like postal offices or identity verification services verify the user owns a legitimate passport and that it depicts the actual face of the applicant. Although this process has been automated over the years, it still requires trust in the state and the verifier, while revealing sensitive biometric data.
Today, the identity problem is more pressing than ever before. Security experts estimate that a staggering 85% of cyberattacks in 2023 were powered by generative AI. This ultimately prompts the question: What can we do to preserve natural identity in the age of artificial intelligence?
From Authoritarian SSN to Libertarian SSI: Three Identity Models
In general, there are three conceptual identity models on the web: A centralized, a federated, and a decentralized identity model. The centralized model involves credentials issued by the government or a trusted authority. For instance, this includes the U.S. SSN, European eID, or German ELSTER for authenticating various .gov among other systems. Trusted authorities, like telecom services, ultimately create scarcity by issuing a limited number of phone numbers. Online, each vendor traditionally managed identities through their own authoritarian authorization methods. Although widely used both offline and online, this approach cannot provide a unified identity layer for the web due to its limited scalability and the inability of any government to enforce a monopoly of violence on the inherently distributed web.
Federated identities represent a more advanced model, introducing a trusted authority known as an identity provider (IDP) between the user and the vendor. Social login options from Google, Facebook, and LinkedIn are examples of this, leveraging the OpenID standard. This article will describe X as one instance of such a system. While the federated model simplifies and secures identity management, it has not yet provided a unified identity layer for the web. This gap led to projects such as Worldcoin, a model at the intersection of federated and decentralized identities, which will be explored later.
The decentralized identity model centers on decentralized data and control across the system, giving users full autonomy over their digital identities without intermediaries. Users can seamlessly transfer identity data between services and control data sharing, akin to the ePrivacy Directive, all on a secure, tamper-proof blockchain. The most prominent instance of this model, called self-sovereign identities (SSIs), require a digital wallet, a Decentralized Identifier (DID), Verifiable Credentials (VCs), and a Distributed Ledger (DLT). Bitcoin and Worldcoin are instances of these systems and are detailed below.
X – The Blue Checkmark
Elon Muk’s leveraged buy-out of Twitter has been one of the top 5 takeovers in 2022 and the biggest ever undertaken by an individual. Next to preserving a free speech zone on the internet, Twitter is a key marketing channel for Musk and a giant opportunity for doing business.
In 1999, Musk launched X.com with the vision of an Everything App. He built a subset of that vision by creating an online Financial Home encompassing banking services, low-cost mutual funds, and peer-to-peer money transfers. In 2000 X.com bought Peter Thiel‘s Confinity Inc. merging their services under the name PayPal.
The domain x.com stayed with PayPal until 2017 when Musk repurchased it due to its high sentimental value. However, it wasn‘t until 2023 that Musk decided to rebrand Twitter to X, announcing the revival of his vision for the Everything App.
But how does this relate to identity management? More and more companies encounter shams, scams, and spams on the web, leading to a 4.3% decrease in online revenue due to bots alone. Imagine a platform like X offering a Proof of Personhood service for app developers – e.g. via blue checkmarks – telling them if account traffic is authentic and monetizable while supporting with user authorization.
Checkmarks could lay the foundation for an Everything App just like WeChat did with its WeChat Pay ID. As with PayPal, each user may be provided with a personal wallet, generating immense business value as companies know they interact with a real, solvent human being. This would ensure their marketing and operational budgets are well spent while protecting their app users from harm.
Elon Musk has already publicly announced his plans to build an identity layer on the web. Right now, a user’s identity is verified by three criteria: Authenticity, Notability, and Activeness. Ultimately, X builds on the physical stack as authenticity is checked by a government-issued ID. This makes the Blue Checkmark digitally non-native, functioning as a secondary layer on the identity stack, built upon the seventh layer of the web stack.
Bitcoin – The Orange Checkmark
Bitcoin was launched by the pseudonym Satoshi Nakamoto in 2009 as a direct response to the financial crisis. He set about building a digital peer-to-peer monetary network – just like PayPal 10 years earlier, but governed by a bottom-up Chain of Consensus, not a top-down Chain of Command. Just as there is no Internet CEO, there is no Bitcoin CEO. Nakamoto disappeared and the network rules.
However, money is just one application of the underlying technology, which is the blockchain. Money is a universal language of value that enables coordination on a scale exceeding Dunbar’s number of 150 social relationships. Thus, a blockchain that is equipped with an incentive mechanism, such as the issuance of Bitcoin currencies, can do far more than just be a slot machine or a pirate haven. Instead of trusting intermediaries like the Federal Reserve, JPMorgan Chase, or Meta Platforms, which confine us within walled gardens protected by positive law and proprietary code, we can rely on fundamental principles of nature: (1) psychological: human self-interest (BTC), (2) mathematical: digital signatures (ECDSA), and (3) physical: conservation of energy (PoW).
The great thing about Bitcoin is that its design counteracts the non-physical properties of the web – it injects friction. In a thermodynamically sound system like Bitcoin, your influence on the network is bound to energy through the PoW mechanism. Thus, creating an arbitrary number of identities serves no purpose, rendering Sybil attacks ineffective. Copying and pasting the ledger or parts of it – creating a double spending scheme – also serves no purpose, as the Nakamoto Consensus incentivizes users to build on the longest chain, establishing it as the single source of truth. Lastly, Bitcoin is trustless, implementing Byzantine fault tolerance where for 3f+1 users, f may be malicious without eroding the network.
As with the blue checkmark, the orange checkmark is closely tied to money. However, rather than paying $8 a month to X, you establish your personhood by linking a wallet with an $X dollar security deposit. Suddenly, property can also be confiscated in cyberspace, deterring misconduct and potentially compensating victims and platform operators for the incurred damage – ultimately equalizing the Accountability Asymmetry.
By connecting your Bitcoin wallet with a browser, each page visit could become a microtransaction, compensating the provider for resource use and making spam prohibitively expensive. Even authenticition is possible through decentralized identifiers (DIDs) implementing specifications such as did:btcr or did:btc. The key idea is that your DID is the ID of a confirmed transaction (TxRef) that sent BTC to a wallet you can prove ownership of through a digital signature. Thus, the Orange Checkmark functions as a digitally native identity layer on the web.
Worldcoin – Using Worldcoins to combat Wordtokens
Ever heard the term “iatrogenesis”? In medicine, this refers to unintentional harm caused by medical treatment or intervention. This, in turn, opens up new business opportunities for “treating the treatment”. Some even claim this is the business model of pharmaceutical companies, keeping the machinery running. Although iatrogenesis originates from medicine, the concept can be applied to any problem-solving entity, including governments, entrepreneurs, or corporate CEOs. Iatrogenics involves examining the consequences of any solution “brought by the healer”. What is the genesis block in Bitcoin thus may be the iatrogenesis block called in Worldcoin.
Being cynical, Sam Altman could also be seen as a “healer.” He promises AGI as a cure to most of our problems. However, on his quest to build AGI, he will inevitably create negative side effects, potentially posing an existential risk to humanity and thus leading to iatrogenesis if the consequences are not a net benefit. In 2019, Altman began addressing one of these side effects by founding Worldcoin. The corresponding Worldcoin Foundation aims to solve issues primarily caused by a set of AI systems he helped create.
While Worldcoin sounds like an Orwellian dystopia to many, it appears to be a genuine approach to creating a universal identity layer. In fact, many parallels can be drawn to Bitcoin. Worldcoin is built on a blockchain with identity commitments and transactions being stored on-chain. The former is generated from a user’s biometric data, similar to how a public key is generated from a private key. The latter records transactions made with the built-in $WLD token, which functions as a governance token and is tradable on decentralized exchanges (DEXs). In the future, it may develop into a global currency, again showing the close tie between identity and money.
Just as Bitcoin is grounded in physical reality, Worldcoin is grounded in biological reality. However, the miners are called Worldcoin Operators and mine coins through scanning irises instead of solving energy-intensive puzzles. Instead of a GPU, they use an ORB to do so. ORBs are biometric imaging devices specifically developed for Worldcoin and can compute a unique embedding based on the user’s iris. This embedding is stored locally in a dedicated wallet but generates an identity commitment that is uploaded to the blockchain and compared against the database to validate uniqueness.
Worldcoin does not handle authentication but can provide Proof-of-Personhood to third-party applications, proving the interacting entity is indeed a human without revealing sensitive identity data. For that purpose, Zero-Knowledge Proofs are used, which reveal no knowledge except that the World App knows the entity is human. Thus, Worldcoin provides an anonymous identity layer on the web grounded in physical reality.